Keep your PACS! Modernize with Affordable PKI
Authentication
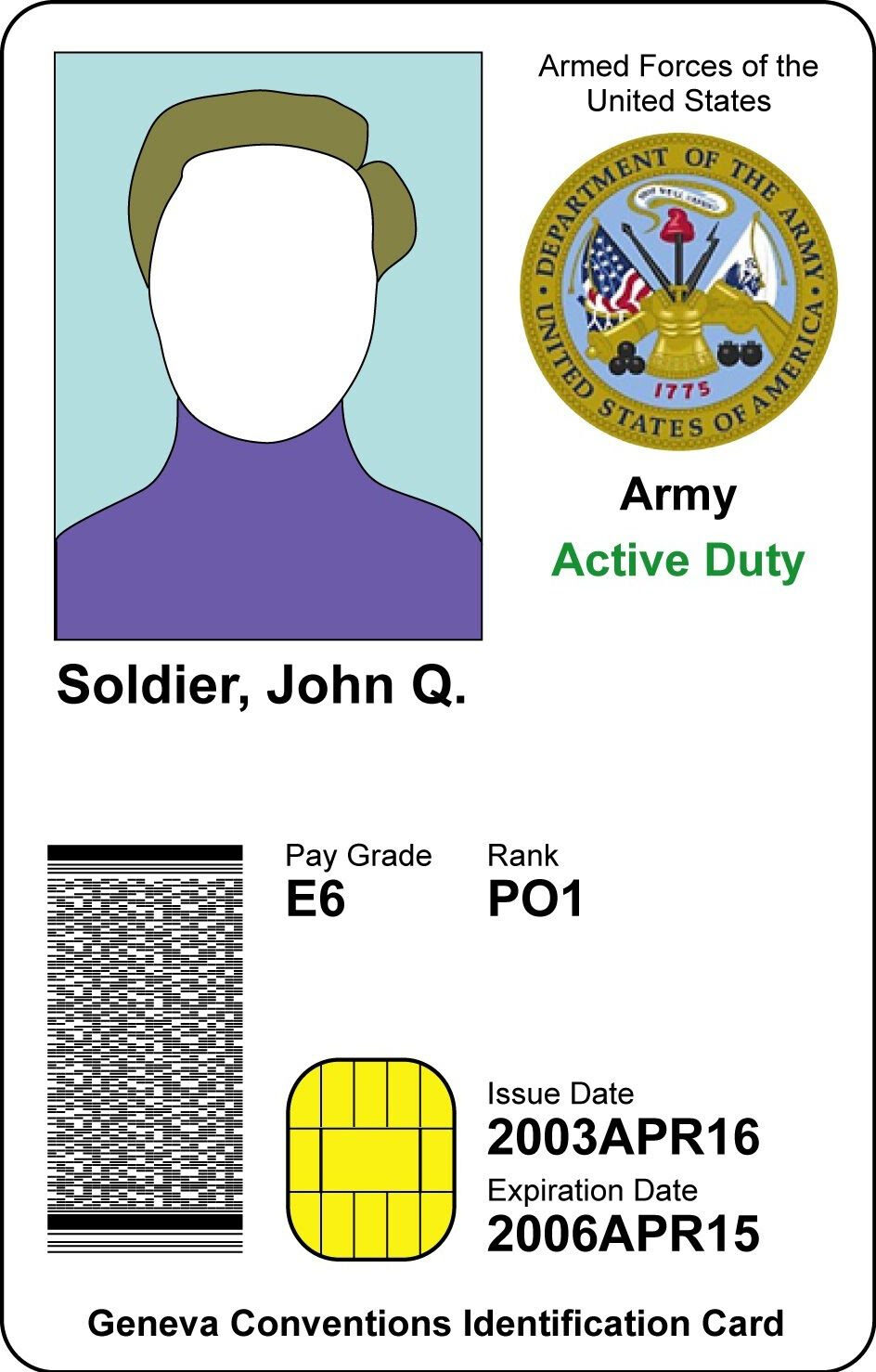
The integrity of a PACS depends on secure data from an ID card. Is the data on your enterprise card secure? That could be a big problem!
Outdated access cards pose major security risks.
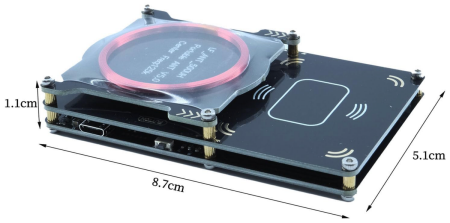
This pocket sized device can copy many widely used access cards in seconds.
Why it matters:
Over 50% of access cards in use today rely on insecure 125 KHz Prox or Mifare classic technology.
These cards pose significant risks for enterprises as they can be easily cloned using an inexpensive device available online.
It is fools gold to replace a PACS without first upgrading to a secure card that is based on PKI technology.
Revolutionizing security with PIV

Many global technology firms are adopting the Personal Identity Verification (PIV) standard, first developed by the US Federal Government. The PIV credential has set a new benchmark for secure access by integrating digital certificates for robust authentication.
Eliminating proprietary cards: PIV does not require secret keys in cards and readers.
Certificate flexibility: Entities can use their own self-issued public key certificates, enhancing control.
PKI verification: Cards can be verified as genuine by PKI-enabled readers through challenge-response and digital signature checks.
The backdrop: Industry solutions like FIDO, PKOC and PK-PACS are adopting the basic PIV platform, pushing the security industry to rethink “PKI in PACS.”
Cost efficiency: Implementing PKI in a PACS is becoming more affordable, rivaling legacy systems.
Seamless integration: PKI operates silently, ensuring credential authenticity without complexity.
Speed trade-off: While PKI may add a second to verify card authenticity, it’s a small price for security.
PKI implementation in PACS:
Driving the news: Implementing PKI in a PACS can be done in three ways, each with its own set of requirements and benefits.
Option 1 – Network of centralized hardware appliances:
Primarily used in the Federal Government on Wiegand systems.
Requires expensive installation of a separate network of PAM appliances that “centralize” certificate status and report it to the PACS panel.
Option 2 – OSDP-based access systems:
Requires PKI-enabled panels and “transparent” readers for centralized PKI processing.
Requires complete system replacement, including OSDP panels, transparent readers, software, and possibly re-carding users.
Network hops can add significant time to access being granted.
Option 3 – Distributed PKI by IDFACTORS:
PKI verification is distributed to each reader for fast local PKI processing.
Less expensive and disruptive: compatible with both Wiegand and non-PKI enabled OSDP panels.
Only requires replacing legacy readers with IDFACTORS readers.
Why it matters:
Each option presents unique benefits depending on the PACS profile, requirements, and budget.
Distributed vs centralized authentication:

In the distributed authentication model, the Door Access Reader acts as the “Verifier” of the card when it’s presented for access. This eliminates the need to forward certificate information to a central access panel, reducing data congestion and speeding up system response.
In contrast, a centralized PKI process requires the access panel to perform cryptographic processing for all connected Readers. This setup necessitates multiple network hops for each Reader, which slows down the verification process and delays access time.
Learn more. Contact IDFACTORS at www.idfactors.com or email customerservice@idfactors.com.